How many times per day do you have to remember your username and password to access an application or Web page? According to a recent TeleSign study, consumers have an average of 23 online accounts, and more avid Internet users have a much higher number. In my own experience, as of noon today, I’ve already logged into 9 different applications - all of which have required username and password authentication. To make matters worse, I had to reset a password to a website I hadn’t used in a while. That said, we at FileOpen know just how frustrating it is to manage what seems is a never ending list of credentials in your head. So today’s post will cover how you can protect your high-value documents without some of the inherent pain points and security issues associated with username and password authentication.

The problem with passwords
Passwords are the most common way users confirm their identities. However, passwords are also considered a weak form of authentication. The truth is that there’s nothing wrong with passwords; the problem is the user. Users experience what is known as password fatigue; they select passwords that are too simple, too predictable, they re-use the same passwords across systems, they fail to change their passwords on a regular basis, and much to our disbelief, users log credentials in notebooks usually kept alongside their machine. As you can see, the Personal Internet Address & Password Log Book retails for $6.49 and is currently a #1 Best Seller on Amazon.
In addition to password fatigue, users fall victim to cybercriminal’s phishing and spoofing scams. And finally, what is to keep a user from lending their credentials to someone else?
FileOpen Approach: Securing documents, without passwords
FileOpen document security software offers businesses a variety of authentication modes designed to alleviate the pain and insecurity of traditional username and password authentication.
The first out-of-the-box mode of authentication is device or machine authentication. With this mode, users authenticate once by opening a FileOpen Registration PDF on their desktop, laptop or iOS device with the FileOpen Client. Once opened, the FileOpen Client sends a list of machine identifiers, unique to that user’s device, to the governing PermissionServer which then logs the information within the user’s profile as a registered device. After opening that registration PDF, all subsequent access requests by that user are permissioned by validating the user’s machine identifiers with the governing PermissionServer. This means the whole identification process is invisible to the user and is exactly the same as opening a non-protected PDF file. All permissions are obtained from the document owner’s PermissionServer in real-time, and are specific to that user’s device. Permissions are not portable in any way that the user can control; permissions are locked to the original device.
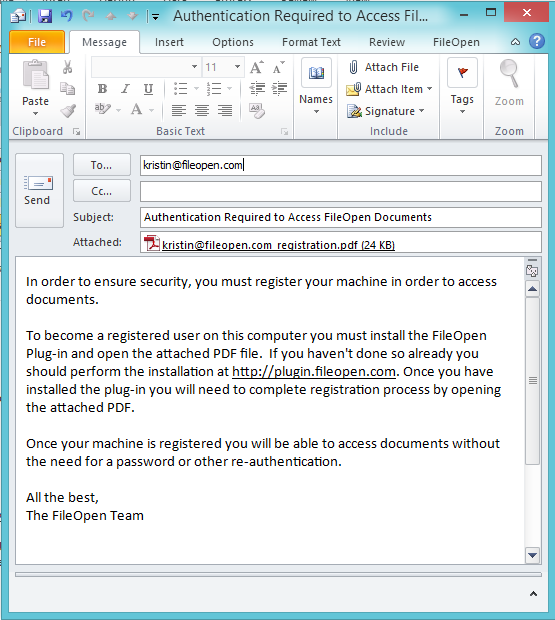
The FileOpen software may also employ additional means of authentication. FileOpen integrates with existing ADS/ SSO systems, eCommerce systems, enterprise file-sync-and-share or learning management tools. These options make it easy for administrators to centrally manage users and permissions, without requiring users to manage yet another password. In addition, custom configurations can be deployed to support cookie-based authentication, domain authentication, and user log-in authentication.
While businesses truly dread the challenges and problems posed by passwords, it still remains a core authentication and security technology. And, as mentioned above, we don’t believe passwords are the root of the problem, we believe it’s the human element. With that being said, FileOpen does support username password authentication and includes features to ensure security. These features include:
- Device limits: Owners may designate the maximum allowable count of devices that user may access a protected document from. The smaller the number the more secure the system.
- Revocation: Allows owners to instantly disable access by document, user or user’s device.
- Tracking: Logs all access and usage by document or user ─ even failed access attempts. This information includes device / machine identifiers, user login, host name, IP address as well as date and time.
- Viewing Requirements: Allows document owners to limit document access to specific operating systems.
- Usage Controls: Prevent or restrict copy/paste, printing, editing, saving and screenshots.
Want to learn more? Start a free 14-day trial to see how you can start protecting your PDFs, without passwords.
